Access Authentication
Sometimes your backend or mock API doesn’t include authentication, especially when you expose the service, so you want to restrict who can access it. Inspectr can introduce a guard, a simple auth layer to secure any service it proxies.
Why Use Inspectr Authentication
Section titled “Why Use Inspectr Authentication”- Shield your API endpoints from unwanted traffic
- Secure exposed, public access to your service without adding code
- Provide temporary auth when the backend lacks it
How It Works
Section titled “How It Works”Start Inspectr with authentication enabled and a secret:
inspectr --auth-enabled=true --auth-secret=mysecretInspectr prints two API key headers in the terminal:
inspectr-auth-key: mysecretinspectr-auth-token: <jwt>Send one of these headers with each request.
| Header | Description |
|---|---|
inspectr-auth-key | Plain secret for quick local testing |
inspectr-auth-token | JWT signed with the secret; expires per --auth-token-ttl |
Both headers act as API keys—include either one with every request.
Requests lacking a valid key or token get 401 Unauthorized.
Token TTL
Section titled “Token TTL”Customize token lifetime (default 24h) when starting Inspectr:
inspectr --auth-enabled=true --auth-secret=mysecret --auth-token-ttl=2A fresh token is generated every run and expires after the TTL.
Example Usage
Section titled “Example Usage”Using the encrypted Key
Section titled “Using the encrypted Key”curl http://localhost:8080/api \ -H "inspectr-auth-key: <key>"Using the JWT Token
Section titled “Using the JWT Token”curl http://localhost:8080/api \ -H "inspectr-auth-token: <jwt>"Tokens and keys appear each time Inspectr starts. Use this feature whenever you need lightweight protection without modifying your backend.
- When to use the key: handy for local development and CI where the secret needs to be private but can be reused without limits.
- When to use the token: safer for public or shared channels because it expires per the TTL. $
Restart Inspectr to rotate the token or set/renew the token and secret from the “Inspectr App” > “Settings”.
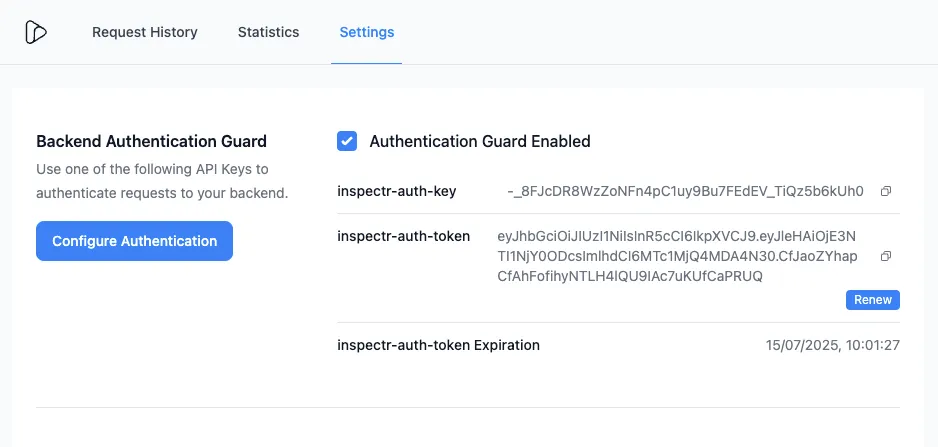
Configuration
Section titled “Configuration”Enable the guard with CLI flags:
inspectr --auth-enabled=true --auth-secret=mysecret --auth-token-ttl=1hOr in .inspectr.yaml:
authEnabled: trueauthSecret: mysecretauthTokenTtl: 1or via the settings in the Inspectr App

